I'm an Information Security Professional with 9 years of experience. My expertise lies in identifying and mitigating security risks across domains, including cybersecurity, infrastructure, data privacy, and DevSecOps. I hold several certifications, including the CISSP certification. I excel not only in technical domains but also in communication and collaboration with cross-functional teams.
Professionally, I've immersed myself in IT for nearly 13 years, dedicating 9 of those years to Information Security. Throughout this time, I've actively participated, contributed, and coordinated tasks, projects, and challenges.
I've refined my ability to identify and mitigate security risks, studying and applying concepts and best practices. As a professional who understands the importance of delivering results, my approach focuses on identifying opportunities for improvement beyond Information Security.
Below, I've separated real quick examples captured from my professional journey, and further down, I've added some subsections with extended information for better illustration:
- Design and implementation of network segmentation, incorporating concepts such as defense-in-depth and microsegmentation.
- Implementation of Single Sign-On through the integration of on-premises AD with Azure AD and Office 365, enhancing user productivity.
- Deployment of Backup/Restore and Vulnerability Analysis Policies.
- Replacement of Microsoft's ForeFront TMG firewall with Watchguard UTM, both at Headquarter and training center for the professional football team.
- Sharing knowledge through internal presentations.
- Hardening on servers and comprehensive revocation of access.
- Automation using GitHub Actions to deploy the application into an AWS EC2 self-hosted agent.
- Automation using Azure Pipelines to deploy the aplication into containers.
- Conversion of the on-premise architecture into IaC using Terraform.
- Deployment of environment with traeffik as a reverse proxy, along with Grafana and Prometheus for dashboards.
- Orchestrated the migration of on-premise file servers to Azure File Share.
- Migration of PHP and .NET applications to containers.
Information security governance involves establishing policies, procedures, and controls to manage risks related to data confidentiality, integrity, and availability. It ensures that security practices align with business objectives and regulatory requirements.
As an information security professional, I've actively contributed to creating a secure environment within organizations. My responsibilities include designing and implementing controls, reviewing internal policies, and promoting security awareness. I actively participate in external audits, maintain detailed documentation, and collaborate on action plans for corrections or mitigations. My expertise extends to ISO standards, audit programs, and the development of clear security policies.
Throughout my career, incident response has been a recurring theme, starting from my initial encounters with ITIL to handling information security incidents according to NIST SP 800-61r2. Incident response is highly relevant and can be found in various frameworks. Even the Brazilian Data Protection Law mandates the existence of incident response and remediation plans.
Let me share a real example where I had to act as an incident handler during an information security incident affecting the Availability pillar of the CIA triad:
After a version upgrade of VMware on our virtualization hosts by the network administration without considering the version discrepancies, seven of our hosts started freezing consistently every week. Even though the impact was diminished by the BC/DR procedure that stated redundancy was mandatory, critical services were disrupted at certain moments. To address this, I delved into the details:
Investigation: I compared information from the hosts that didn't experience issues. I meticulously reviewed logs, timestamps, and system configurations to identify patterns.
Root Cause Analysis: Analyzing release notes for each VMware version, I discovered a critical change. VMware had transitioned from using emulation (vmklinux + legacy driver) for communication between the kernel and hardware to using a native driver.
Solution: I recommended purchasing a new network card with native support. We bought one for testing, and it successfully resolved the freezing problem.
Mitigation: To ensure stability across all hosts, we initiated buying one new network card with native support per month until all hosts were corrected.
In the previous example, resolving the incident involved some steps: Investigation, Root Cause Analysis, Solution, and Mitigation. This is just one instance, in an environment where numerous incidents could occur daily, implementing an effective incident response plan is crucial and to accomplish this goal consulting frameworks is really recommended.
NIST SP-800-61r2 incident response lifecycle:

As each company has its own characteristics, there's no one-size-fits-all recipe for creating an incident response plan. For instance, small businesses may lack the resources to deploy SIEM or SOAR systems, while larger companies find them essential for handling thousands of daily events, alarms, and incidents. However, there are generic items that should be included in any incident response plan, such as: roles and responsibilities incident categorization, incident handling procedures, detection and reporting, evidence handling, documentation and contact Information.
In conclusion, planning, learning from past incidents, regularly reviewing and refining the plan are essential for a good incident management and, of course, business continuity.
Before the creation of the General Data Protection Law (LGPD) in 2018, I lacked clarity on what privacy meant and how it differed from information security. However, with the LGPD coming into effect in 2020, I felt the necessity to delve deeper. I read books, took courses, and pursued certifications to enhance my knowledge in this critical area.
In simple terms, privacy refers to an individual's ability to control the disclosure and accessibility of their personal information. To ensure privacy, we implement information security measures. In essence, while privacy is the objective, information security is the means to achieve it.
The LGPD is Brazil's data protection law and is hugely based on the european General Data Protection Regulation (GDPR). Both regulations share common principles, such as the right to be informed, the right to access personal data, the right to erasure, among others. On the other side, they differ on some aspects, for example: extraterritorial scope, legal bases for processing, penalties and notifications for violations, etc.
Similar to any other framework implementation, complying with the LGPD may demand substantial effort, depending on the company's existing practices and gaps. Additionally, addressing the requirements should be treated as a project, taking into account realistic deadlines, expected outcomes, and collaboration among cross-functional professionals, including: privacy and information security professionals, process analysts, lawyers, project managers.
The cross-functional collaboration is fundamental due to the necessity to act, create, and maintain documentation and processes, such as:
Establishing Data Flows and Personal Data Inventory
Reviewing Contracts and Sector-Specific Regulations
Review cross-border data transfer agreements
Data Protection Impact Assessment (DPIA)
Privacy Policy (Data Protection)
Privacy Training and Awareness Program
Cookie Policy
Handling Requests, Complaints, and Corrections
Creating processes to address data subject requests, complaints, and rectification
Consent Forms for Data Subjects and Parents (if applicable)
Incident Response and Remediation Plan
Action Plans
Additionally, it's essential to establish a routine that fosters continuous improvement, allowing every critical analysis to refine the LGPD alignment.
It's also important, beyond the expertise necessary for professionals, to highlight terms that every individual should know, they are:
The data subject - It refers to an individual who can be directly or indirectly identified by one or more factors.
Rights of the Data Subject - It empowers individuals to control how their data is collected, processed, and used by organizations.
Personal data - This encompasses any information that can identify a person.
Sensitive personal data - A special category of data related to racial or ethnic origin, political opinions, religious or philosophical beliefs, union membership, genetic or biometric data, health, sexual life, or sexual orientation.
Anonymization - The process by which data can no longer be linked to the data subject. It is irreversible and often used for statistical purposes or research.
Pseudonymization - When data cannot be attributed to a data subject without additional information. For example, encryption is a form of pseudonymization.
Processing of personal data - Any operation or set of operations performed with personal data, whether automated or not.
Personal data breach - A security incident that leads to accidental or unlawful destruction, loss, alteration, unauthorized disclosure, or access to personal data transmitted, stored, or otherwise processed.
Supervisory authority - The body responsible for overseeing compliance with data protection regulations in companies.
Controller - The entity responsible for determining the purposes and means of processing personal data. It can be an individual, legal entity, public authority, agency, or other body.
Processor - An entity (individual, legal entity, public authority, agency, etc.) that processes personal data on behalf of the controller.
Legal bases - Requirements for lawful processing of personal data. At least one legal basis is necessary for legitimate processing.
Data Protection Officer (DPO) - The professional responsible for handling personal data and acting as the point of contact with data subjects and the national authority.
Minimization - Personal data should be adequate, relevant, and limited to what is necessary for the purposes for which it is processed.
Subsidiarity - Personal data can only be processed when no other means can achieve the intended purpose.
Really interesting, isn't it? In summary, the General Data Protection Law (LGPD) is a crucial framework for safeguarding individuals' privacy rights and ensuring responsible data handling. Companies must proactively comply with LGPD provisions, prioritize data protection, and foster a culture of transparency. By doing so, they contribute to a safer digital environment for all.
Dealing with users (employees, customers or suppliers) is always a challenge, as unlike our computers, humans have some more complex variables, such as: mood, temperament, personality and etc.
Although it is challenging, it does not have to be a battle to deal with users. Throughout my professional experience, I had the privilege of supporting different types of people, from broadband service customers (call center) to company presidents. Today I see how enriching these contacts were.
Well, before proceeding you must keep in mind a fundamental point: people are the most important pieces of a company and for us in Information Security, it is no different. Users are decisive for the success or failure of projects in our area, so proper communication is essential to maintain a good relationship with them.
Based on the experiences I had, I listed 5 points that I believe are important when establishing a relationship with users in information security.
THINK LIKE A USER
Despite seeming simple, it is very important to put yourself in the user's position and try to
understand from their
perspective the information that will be transmitted, be they, through awareness campaigns,
implementation of
procedures, policies or through lectures.
The infamous phrase: "I am responsible for what I say, not for what you understand" so common on social
networks,
has no place here, you should explore different ways to make yourself understood. "To beat a hacker, you
must think
like one", adapting to our scenario: "To talk about information security with a user, you must think
like one", put
yourself in the place of the person who will receive the information or guidance.
USE CREATIVITY
Avoid boring and tedious content, especially in awareness campaigns. Swap giant texts for
self-explanatory, colorful
and interesting images. Try to arouse your user's curiosity by making them want to continue learning
about the
subject. Use practical examples, if you want to guide on the use of passwords, show some techniques that
hackers use
for this purpose, the same can be done with phishing, ransomware and other subjects.
Develop an information security booklet with less formal content. In this booklet opt for images and
informal texts,
as this way it will be much more pleasant to read.
LISTEN TO USERS
Talk to users, be willing to listen to suggestions and complaints, these conversations are great for
having ideas
and also to be able to guide the user on a certain subject.
It is also important that the professional who will relate to the users has the skill for it. Sympathy
and Charisma
are fundamental. I strongly believe in the existence of different types of intelligence and the main one
in this
context is interpersonal intelligence. People with this type of intelligence are good for communication,
as well as
understanding the feelings and motivations of others.
CREATE GOOD EXAMPLES
It can be very demotivating for the user who follows the correct security procedures to see that their
peers ignore
them. Security controls must be followed by everyone, regardless of positions or functions.
Remember that a good example is the best way to teach someone. So, try to bring managers and directors
to your team
and let them be the good examples. Anyone who has participated in the implementation of an information
security
management system knows that their participation and commitment are fundamental to the success of the
project.
DON'T BE BORING
Finally and no less important: don't be boring. Even if you are good at interpersonal relationships, be
careful,
because we can all be inconvenient at certain times. To not be the boring one of information security:
think like a
user, listen to them and be creative.
Let's assume a hypothetical scenario:
Michael was contracted to maintain a web application with the sole requirement that its availability
must be 99.9% per year.
The environment minimally demands one server (for both the application and database) and one
internet link. If successful, Michael earns $100,000 per year; if he fails, $50,000 is deducted from
his earnings. Any costs to enhance resilience will be deducted from the $100,000.
Michael sees a great opportunity to make money, and accepts the job.
This is a mental exercise that allows us to explore different possible outcomes: Has Michael
succeeded or failed?
Availability is one of the pillars of information security, as important as confidentiality and
integrity. When we talk about business continuity and disaster recovery (BC/DR), availability takes
center stage.
BC/DR are distinct processes, but are often referred to together. While the first focuses on keeping
the organization running, the latter focuses on restoring the organization to a normal state. Both
involve a combination of plans, policies, and procedures to ensure the organization's resilience when
facing events that can disrupt its functions.
Having worked in infosec and IT for many years, I've gained valuable experience from various
disruptive incidents. These include software misconfiguration, hardware failures, supply chain or vendor
issues, cyberattacks, and natural events. Such events can significantly impact an organization's
critical functions, potentially affecting its reputation and revenue.
To contain or at least minimize the negative impact, organizations implement, partially or entirely
a set of practices known as business continuity management (BCM).
It is important to mention that many organizations, especially small ones, adopt technical controls
to ensure availability, even if they are not fully aware of the importance of BCM. Examples include
RAID, hardware and link redundancy, UPS/generator contingency plans, regular backup routines, and mirror
sites/zones.
Now, returning to the hypothetical scenario, has Michael succeeded or failed? As a mental exercise, different approaches and results are possible; everything depends on our imagination in building scenarios of success or failure. Let's see two possibilities.
Scenario of Failure:
Michael disregards the availability requirement (99.9% per year). He takes the server home,
increases his internet speed to 1Gbps with his ISP (Internet Service Provider), and thinks it will be
sufficient. However, two months later, an unexpected power outage affects his neighborhood for two days
while he is out of town, ending his chance to get the full money.
Remember, this is a hypothetical scenario with the only requirement being 99.9% availability per
year. This means there is only a downtime window of 8 hours and 45 minutes. Not even datacenter Tier I
(99.671%) and Tier II (99.741%) guarantee this uptime.
Let's explore a different approach that leads to success:
Scenario of Success:
Michael also takes the server home, however he recognizes that the permitted downtime is
insufficient to mitigate the risks inherent in an environment comprising a single server (handling both
application and database) and a single internet link. Therefore, Michael decides to apply some practices
from BCM:
He conducts a business impact analysis (BIA) to identify the critical functions and their financial
impact in case of disruption:
Critical function: Ensure annual downtime is less than 8 hours and 45 minutes.
Financial impact: Loss of $50,000 in earnings.
Additional impact: Partner dissatisfaction.
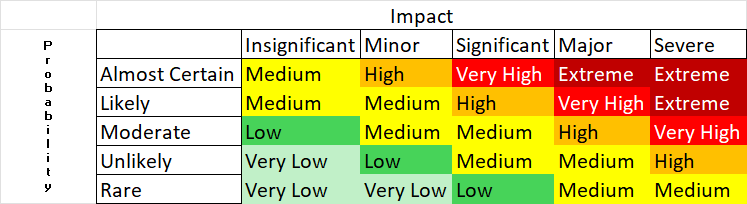
Next, he conducts a risk evaluation using the current assets to pinpoint single points of failure and
other potential risks:
Rist Matrix
Risk Registers
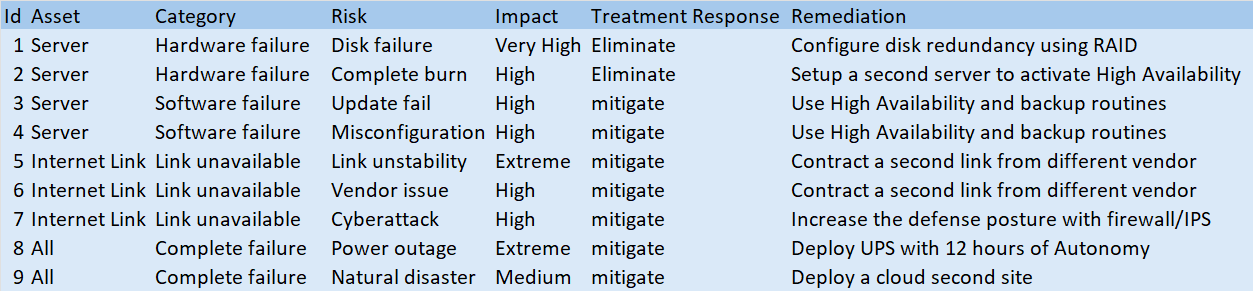
Lastly, he creates a simple BC/DR plan, considering:
Maximum allowable downtime (MTD): 8 hours and 45 minutes
Recovery time objective (RTO): 3 hours
Recovery point objective (RPO): 2 hours
Additionally, the BC/DR plan states:
- Implement intrinsic monitoring between the on-premise and cloud environments with alert
capabilities.
- Set up a backup routine to run every 2 hours, both on-premise and in the cloud.
- Test the recovery capability within the RTO on a monthly basis.
- If unavailability exceeds 10 minutes, activate the cloud site.
After a year of minor issues and a $20,000 investment to enhance resilience, Michael earns $80,000. Due to his good performance, his partner offers an additional 2-year contract, doubling his compensation to $200,000 while maintaining the same deductions.
Isn't it nice to see Michael succeed?
Michael's journey underscores the critical importance of availability. While the case study is hypothetical, it mirrors real-world scenarios where failing to meet SLAs or neglecting best practices can lead to contract losses, reputational damage, and financial penalties. Striking a balance between income and investments in information security is a challenge that organizations face, regardless of their size.
In conclusion, ensuring availability and strategically implementing (BC/DR) plans are crucial. During my years of experience in infosec and IT, it's evident that prioritizing these elements can significantly contribute to enhancing operational resilience. Thus, by bringing availability into play and investing in BC/DR strategies, organizations can avoid potential losses and ensure long-term success and sustainability in today's competitive landscape.
ISO/IEC 27001 is one of the most relevant and recognized frameworks in information security. Widely adopted, this standard defines the requirements and controls necessary to establish an information security management system (ISMS). Additionally, it allows organizations to be certified, demonstrating their commitment to secure practices.
The ISO/IEC 27001 (2022) document is concise, with just 19 pages (clauses and Annex A) in its English version. Within the document, there are 10 clauses, with those from 4 to 10 being relevant to the ISMS. They are:
4. Context of the organization
5. Leadership
6. Planning
7. Support
8. Operation
9. Performance evaluation
10. Improvement
These clauses establish the essential elements to initiate and maintain the management system (subclause 4.4).
The following image illustrates this idea from a macro perspective:
As seen, the image comprises three major sections: top management support, scope, and core components.
Let's break them down:
Top Management Support
Top management support acts across the organization boundaries and plays a vital role. From the standard's clauses, it is possible to see that they must:
- Demonstrate leadership and commitment through various means (5.1)
- Establish the information security policy (5.2)
- Ensure responsibilities and authorities are assigned (5.3)
- Review the organization's information security management system regularly (9.3)
Furthermore, while not mentioned explicitly, the following clauses suggest top management participation:
- Establish the information security objectives (6.2)
- Determine and provide the necessary resources (financial or otherwise) (7.1)
- Ensure employees are aware of the information security policy and their contributions to the effectiveness of the ISMS (7.3)
Scope
The scope is another crucial element. Here, the boundaries and applicability of the ISMS are set. This involves considering the subclauses within Clause 4, Context of the Organization:
- Consider the external and internal issues (4.1)
- Determine the interested parties and their requirements (4.2)
- Establish the scope (4.3), considering items 4.1 and 4.2, as well as the interfaces and dependencies existing between activities
Core Components
Last but not least, the Core Components within the scope comprise mandatory elements crucial for a secure posture:
The ISMS uses a risk-based approach defined in the following clauses:
From Clause 6 (Planning) and Clause 8 (Operation), we have:
- Actions to address risks and opportunities (6.1)
- Information security risk assessment (6.1.2 and 8.2)
- Information security risk treatment (6.1.3 and 8.3)
Clause 6 outlines the planning of risk management, including criteria, tolerance, and security levels. Clause 8 addresses the operation of risk management.
Identified risks determine which Annex A controls should be implemented. All controls from Annex A should be considered with justifications for their inclusion or exclusion in a Statement of Applicability.
Additionally, ISO/IEC 27001 mandates continual improvement (10.1), which is key to evolving and maturing the ISMS over the years. The following requirements support this approach:
- Act when a nonconformity occurs and take corrective actions (10.2)
- Monitoring, measurement, analysis, and evaluation (9.1)
- Conduct internal audits (9.2)
- Management review (9.3)
Additional important requirements within the Core Components add consistency to the ISMS:
- Planning of changes (6.3)
- Competence for those working within the ISMS (7.2)
- Awareness (7.3)
- Communication (7.4)
- Documented information (7.5)
In conclusion, ISO/IEC 27001 provides a comprehensive framework for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS). By adhering to its structured approach, organizations can effectively manage and mitigate risks, ensuring the confidentiality, integrity, and availability of their information assets.
The standard's emphasis on top management support, clear scope definition, and core components such as risk management, applied controls, and continual improvement underscores its holistic nature. This not only helps in achieving compliance but also fosters a culture of security within the organization.
Information Security Governance:
- Risk assessment
- Creation of controls and review of internal policies.
- Awareness campaigns for information security.
- BC/DR procedures
- Participation in audits.
Vulnerability Management:
- Vulnerability analysis (Tools: Nessus, OpenVas, Nikto, Dirbuster, Burpsuite, nmap,
metasploit, among others).
- Penetration test analysis and feedback.
- Documentation and action plan creation for corrections or mitigations.
Firewall, Antivirus, and Backup Management:
- VPN, Proxy, and IPS Management.
- Deployment, maintenance, and updates.
- Backup routine management.
DevSecOps Practices:
- Infrastructure as Code (IaC).
- Pipelines and automations (Python, Shell Script, and PowerShell).
- Containerization of PHP and .NET applications.
- Developer support / Code analysis.
Administration of Azure, AWS an on-premise environments.
Meetings with Clients and Suppliers.
- Development of Information Security Policy (ISO/IEC 27001).
- Awareness campaigns for information security.
- Responses to information security incidents.
- Firewall, antivirus (console and endpoints) and backup management.
- Vulnerability analysis (Tools: Nessus, OpenVas, Nikto, Dirbuster, Burpsuite, nmap,
metasploit, among others).
- User support.
- Network administration.